Contact us
- Home
- Solutions
Managed Security Services
Industry Focus
- Company
Cybersecurity for a digital world
- Case studies
- Resources
Fortifying Your Defenses with Precision
of Cybercrime Resolved
Security Assessments
Completed
Cases of Cybercrime Resolved
Security Assessments Completed
Compliance Audits Done
Penetration Tests Completed
Dive into our innovative A4 approach – Assess, Audit, Assure, Apply – where we meticulously fortify your digital fortress. With precision, we dissect vulnerabilities, audit systems rigorously, assure compliance seamlessly, and apply bespoke solutions, ensuring ironclad protection in an ever-evolving threat landscape.
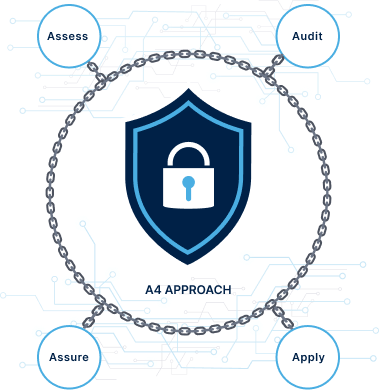
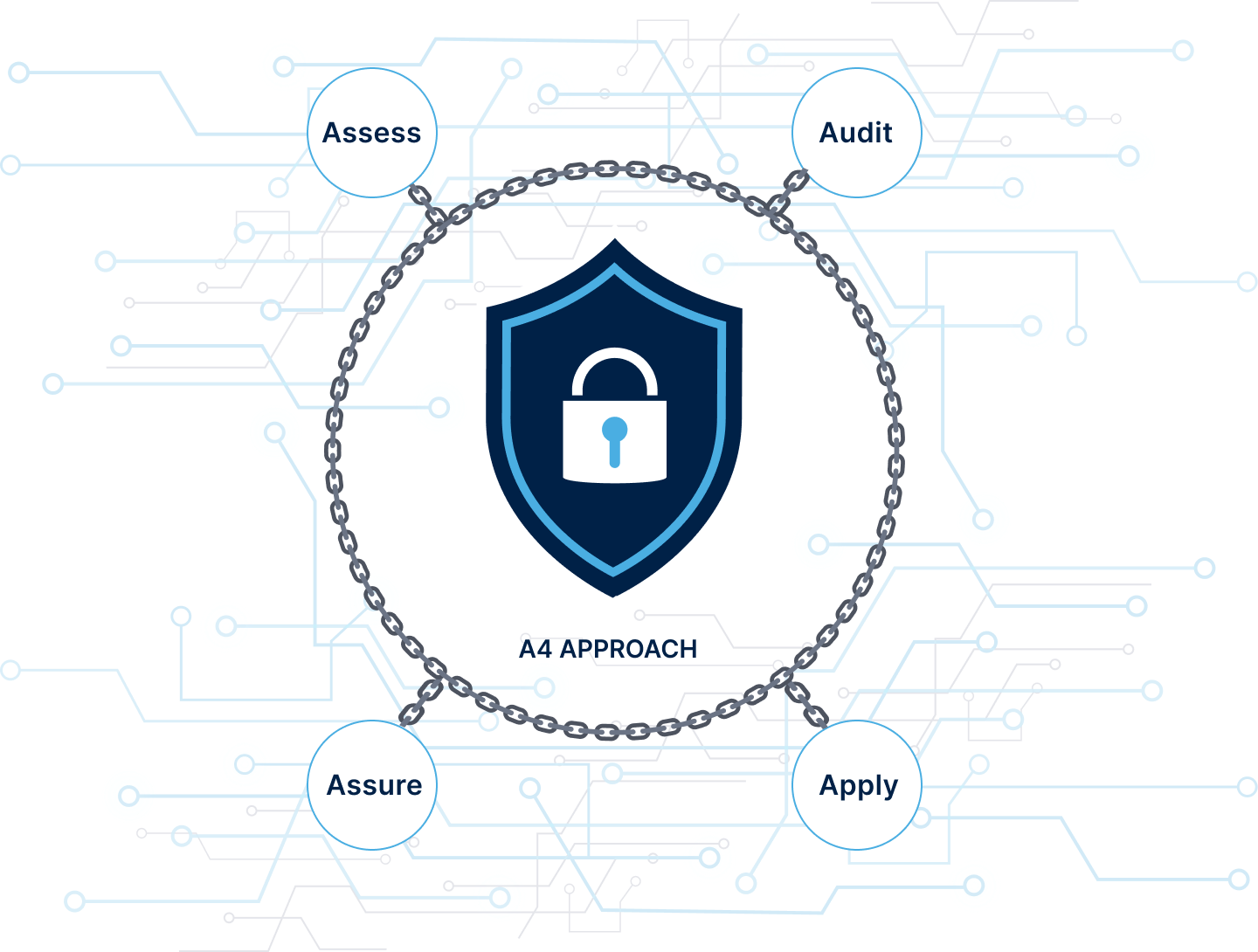

We meet with a client to assess their security system needs, objectives & business rules. This often includes an investment-grade testing of existing security systems that may be integrated for a seamless security solution. This may include integration of existing security, building management, IT, HR or other systems as necessary.

We determine the realm of possibilities within the confines of project timelines, budgets, and the desired system performance. We meet with key business stakeholders, define the security architecture, and deliver a detailed strategic plan as per their compliance requirement.

Detailed plans and Architecture designs are developed that include all technology and system components necessary to deliver the final solution. This formal documentation is then approved and distributed to the SADI (Security Architecture Designing and Implementation) team.

At Cycops, professional Project Management is crucial to the successful delivery of each security solution. The assigned Site engineer is responsible for the client relationship and to ensure a client's satisfaction throughout the maintenance phase

We meet with a client to assess their security system needs, objectives & business rules. This often includes an investment-grade testing of existing security systems that may be integrated for a seamless security solution. This may include integration of existing security, building management, IT, HR or other systems as necessary.

We determine the realm of possibilities within the confines of project timelines, budgets, and the desired system performance. We meet with key business stakeholders, define the security architecture, and deliver a detailed strategic plan as per their compliance requirement.

Detailed plans and Architecture designs are developed that include all technology and system components necessary to deliver the final solution. This formal documentation is then approved and distributed to the SADI (Security Architecture Designing and Implementation) team.

At Cycops, professional Project Management is crucial to the successful delivery of each security solution. The assigned Site engineer is responsible for the client relationship and to ensure a client's satisfaction throughout the maintenance phase
We’re happy to answer any questions you may have and help you determine how our services best fit your needs.
Email Us : info@cycops.co.in
We Schedule a call at your convenience
We do a discovery and consulting meting
We prepare a proposal